
The OBD (On-Board Diagnostics) port in every modern car serves as a gateway to the vehicle’s internal systems.
Mechanics use it to diagnose engine issues, check error codes, or reset warning lights.
Insurance companies and fleet operators also rely on it for data collection. However, criminals have begun targeting this small but powerful access point.
Recognizing signs of tampering can help car owners prevent theft, fraud, or future system failure.
If you are already dealing with car access issues or a lost fob, MR-Key offers trusted car key replacement services. Staying ahead of potential vulnerabilities begins with protecting both the key and the digital access points inside the vehicle.
Knowing what the OBD port controls—and how intruders exploit it—prepares you to take action.
What Is the OBD Port and Why It Matters
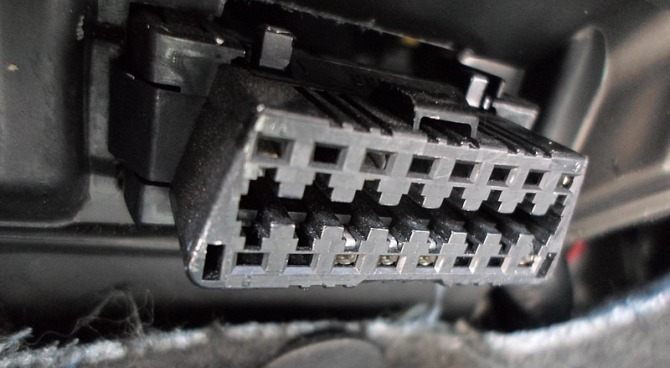
Every car built after 1996 includes a standard OBD-II port, usually located under the dashboard near the driver’s side. It connects diagnostic tools directly to the vehicle’s computer systems. Through this single connection, a person can:
- Read and clear engine codes
- Monitor emissions data
- Adjust engine parameters
- Access the ECU (Electronic Control Unit)
The port was never intended for security purposes. Its primary function is maintenance. Unfortunately, the direct connection to vehicle software also allows hackers and thieves to manipulate essential systems, especially in vehicles without encrypted communication protocols.
Common Reasons for OBD Port Tampering
Criminals and bad actors target the OBD port for several purposes:
- Key Cloning: Thieves can connect devices that generate new keys or overwrite digital security profiles.
- Mileage Rollback: Fraudsters can reset odometer values to increase resale prices.
- System Unlocking: Some use the port to bypass security features, disable alarms, or unlock immobilizer settings.
- Fleet Tracking Disruption: In company cars or rentals, tampering may stop data collection or block location tracking.
The potential for misuse increases when vehicles are parked in public spaces or left unattended for extended periods. High-end and late-model vehicles face greater risk due to higher resale value and greater compatibility with hacking tools.
Physical Signs of Tampering Near the OBD Port

Inspect the area under the steering column regularly. Common indicators of tampering include:
- Loose Plastic Panels: The dashboard panel covering the OBD port may not sit flush or may appear forced open.
- Scratches or Tool Marks: The area around the port may have visible scuffs or pry marks.
- Unfamiliar Connectors: Extra wires or plugged-in devices that do not belong to you or your mechanic can signal intrusion.
- Missing Dust Cap: Some ports come with a small protective cover. Its absence may point to recent access.
- Signs of Heat Damage: Burnt plastic or discoloration around the port may suggest improper device use or high-voltage connection.
Always compare the current state of the OBD port area with its usual appearance after professional service visits. Take photos for reference after routine maintenance, especially if you park on public streets or use valet services.
Electronic Symptoms Suggesting Unauthorized Access
Even if physical signs are absent, the vehicle may begin to behave oddly. Electronic symptoms of tampering include:
- Unexplained Warning Lights: Sudden check engine lights without noticeable performance changes.
- Dashboard Glitches: Clock resets, incorrect fuel readings, or instrument cluster delays.
- Changes in Drive Behavior: Altered transmission shifts, power output, or engine responsiveness.
- Odometer Irregularities: Mileage that does not match service records or personal logs.
- Loss of Custom Settings: Seat positions, radio presets, and display themes reset without cause.
Some changes may be subtle, especially if a skilled intruder covers tracks using high-end hacking tools. In such cases, a professional scan or service audit becomes essential.
Types of Devices Used in OBD-Based Attacks

Understanding the tools used by attackers helps identify abnormal hardware or cable types:
- Key Programmers: Devices like Autel, Launch, or SKP-900 can clone or erase key profiles in minutes.
- Mileage Correction Tools: Units designed to rewrite odometer readings, especially on digital dashboards.
- ECU Flashers: Tools that alter the software of the car’s main control unit, used for tuning or disabling safety features.
- CAN Bus Bridges: Devices that intercept or inject false data into the vehicle’s communication system.
- Remote Access Dongles: Some plug-and-play units include SIM cards or Wi-Fi modules for remote hacking.
Always monitor for new devices plugged into the OBD port, especially in shared vehicles or fleet operations. Ask mechanics to document any diagnostics and remove equipment after use.
How to Secure the OBD Port
Complete protection involves both physical barriers and electronic safeguards. Recommended steps include:
Use an OBD Lock
Aftermarket OBD locks physically block the port with a tamper-resistant case. Most use metal enclosures that fit over the connector and require a key to remove. Some models replace the factory port with a decoy and relocate the real one to a hidden area.
Install an OBD Blocker Relay
This type of relay blocks access unless the vehicle is unlocked using the proper remote. It cuts power to the port entirely or disables communication until valid access occurs.
Hide or Relocate the Port
In fleet vehicles or high-risk zones, some owners relocate the port to a concealed area. The original location may contain a dummy connector. This method stops quick plug-in attacks.
Enable Factory Security Features
Newer vehicles include settings that limit diagnostic access without proper authorization. Some require login credentials or pairing confirmation. Always consult a dealership to enable these protections.
Add Aftermarket Immobilizers
Independent immobilizers block engine start even if a cloned key is present. They require a separate code, RFID tag, or smartphone signal to activate the ignition system.
Legal and Warranty Considerations

Tampering with the OBD system can violate warranty agreements, insurance terms, and state regulations. If you suspect unauthorized access:
- Document all visible evidence
- Contact your insurance provider
- Visit an authorized service center for diagnostics
- Request a scan tool report or ECU access log if available
Early detection helps maintain warranty coverage and avoid being blamed for alterations you did not approve.
What to Do if You Suspect Tampering
Immediate action limits potential damage:
- Avoid Driving Until Scanned: Software changes can affect fuel injection, braking, or steering.
- Record All Findings: Photos, videos, and written notes help build a report.
- Check All Personal Keys and Devices: Ensure nothing has been lost or replaced.
- Request Access Logs or Scan Reports: Professional shops may detect tampering signatures.
- Contact Law Enforcement if Theft Occurred: If the car was stolen and recovered or if valuables are missing.
Be proactive with regular inspections. Install dash cameras with motion detection if you park in public spaces for extended hours.
Conclusion

The OBD port plays a key role in modern vehicle diagnostics, but it also presents an often-overlooked security risk.
Criminals exploit it to clone keys, alter mileage, or bypass safety systems. Knowing how to spot tampering can help protect your car from theft, data loss, and performance issues.
Stay alert to physical damage, unfamiliar devices, and sudden electronic glitches. Implement practical safeguards such as locks or relay switches to secure access.
For peace of mind, perform periodic checks or ask your mechanic to inspect the port during routine maintenance.





